¶ Overview
The Defend-O-Tron is a security device intended for small to medium size businesses that don't have budgets or staff for protection devices or subscriptions from tier level vendors such as Cisco, Juniper, Fortinet, Sophos, etc. We’re attempting to bridge the gap with a more affordable yet equally effective solution.
It works by detecting at two different levels unauthorized connection attempts, blocks them and reports that bad actor to a central location that in turn relays the address of the bad actor to other users of our device so they receive updates of potentially unwanted traffic. This way the whole ecosystem stays updated from every other connected device. This is a sharing scenario instead of an isolated one, thus making each device a contributor and consumer to preventing unwanted and bad actors from illegally connecting to your network.
The heart of the Defend-O-Tron is powered by Crowdsec and it’s firewall “bouncers”. This is augmented with Suricata an Intrusion Detection System (IDS) that actively scans traffic across the ISP-OUT interface (Traffic from your local network to the internet) and the ISP-IN interface (Traffic incoming from the Internet to your router/firewall device).
When traffic from the internet comes into the Defend-O-Tron it’s inspected BEFORE reaching your router and local network. If it’s determined by the IDS rules that the traffic coming in is unwanted or malicious then the IP address of the offender is immediately blocked and stopped silently, they will just see a closed stealth port. This information is then sent for further analysis to Crowdsec’s global information systems. Here it is inspected via artificial intelligence (A.I.) and then upon verifying the legitimacy of the offender, this information is shared amongst all the other Defend-O-Tron devices connected to Crowdsec. This way everyone’s device will receive information about bad actors in real-time and will update the local rules on the device.
¶ Protection Flow
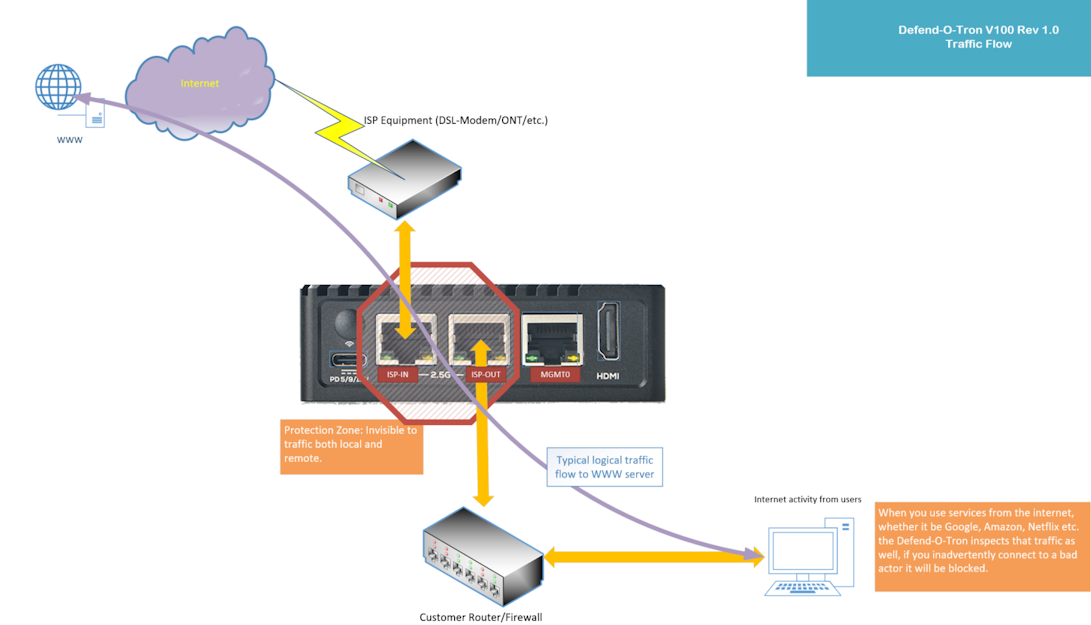
The Defend-O-Tron is transparent to traffic from the ISP to your router/firewall, making any bad actor unaware of it’s presence.
No extra software to install and no special configurations make this a simple design. This allows the Defend-O-Tron to be removed quickly in the event that it could be interfering with data flow to or from the internet, while still being accessable via the management interface. Simply plug your firewall/router back into the ISP equipment as before.
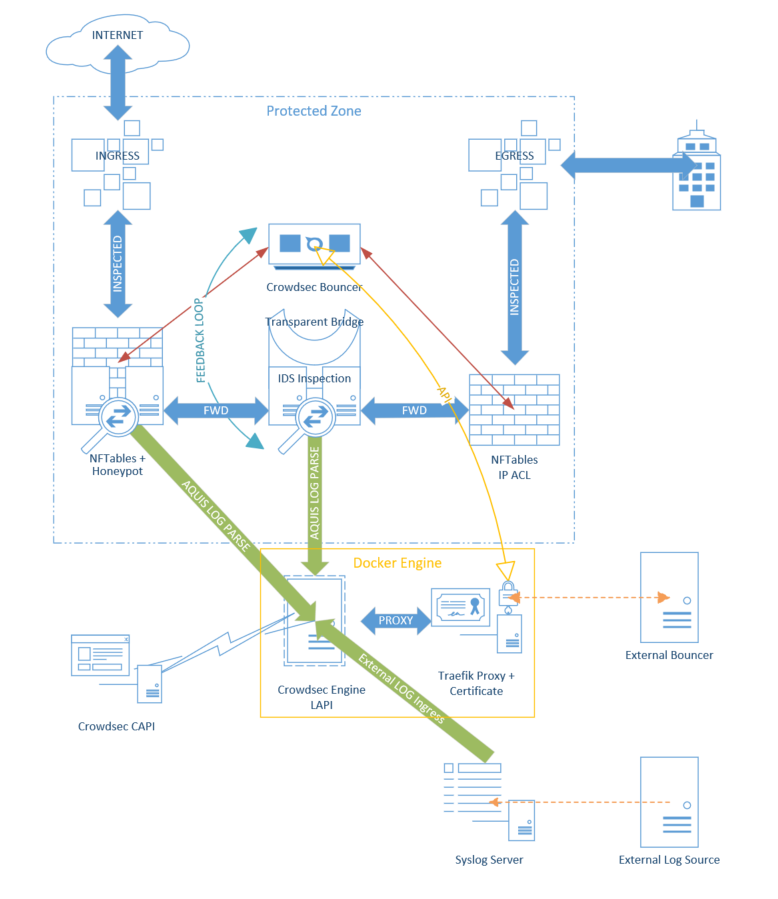
¶ Protection Architecture
Here is the system architecture based on the protection flow. Most of the components are Docker containers further isolating them to protect the system.
Defense Components (installed directly in the OS):
- Crowdsec Firewall Bouncer (NFT)
- Suricata
- NFTables and rules
- NFT Logger Ulogd2
- RSyslog
¶ Quick Report
A quick port scan to the router reveals this report from GRC.com Shields Up
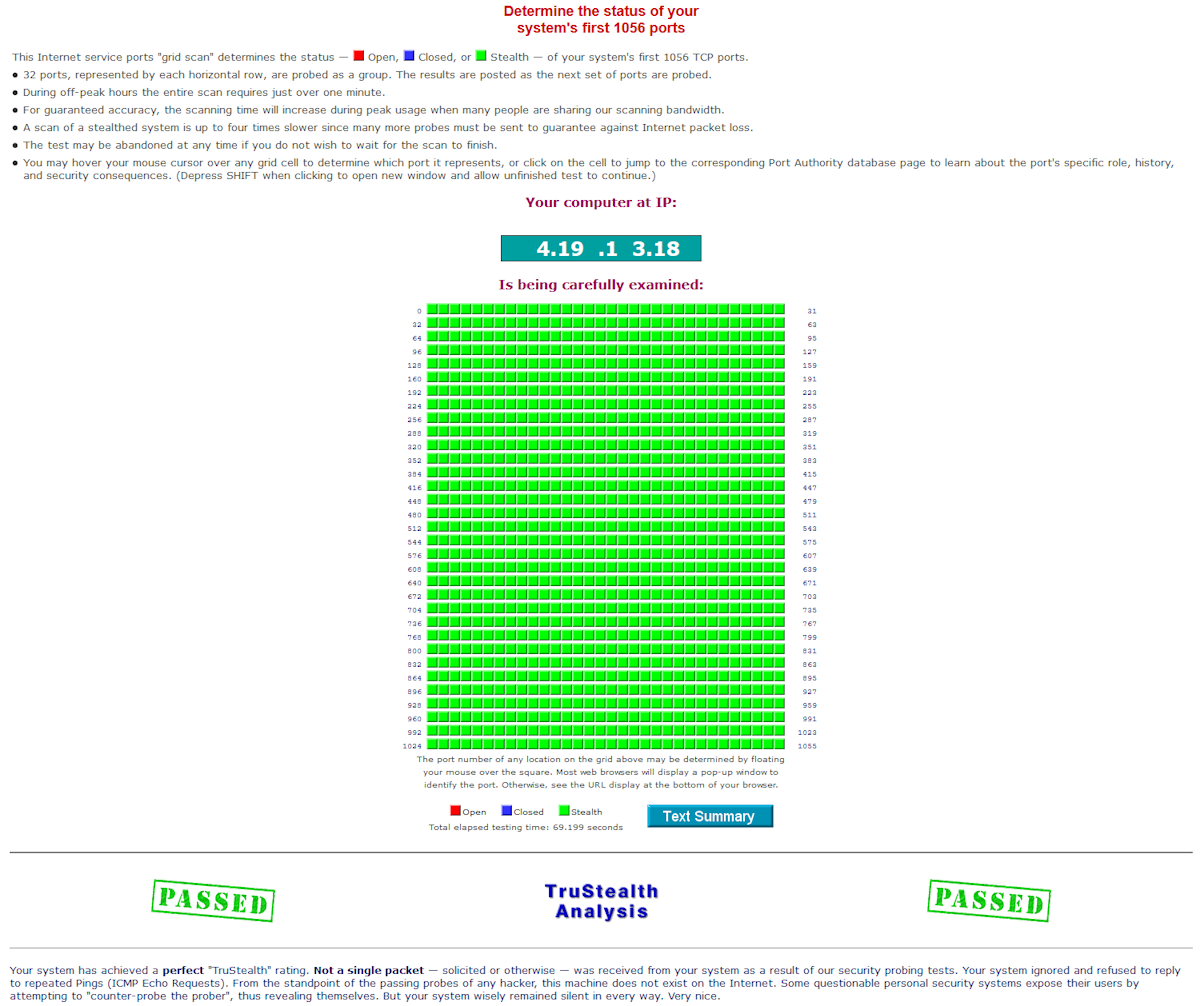
This report gives a full True Stealth rating as the ports are blocked and the firewall/router does not accept pings (ICMP Echo). Your report may vary depending on the ICMP configuration you have.
¶ Getting Started
Your Defend-O-Tron security device is quick and easy to install. You should be up and running in no time.
- Features Worry free defense.
- Requirements Networking and connections.
- Installation Guide Detailed installation instructions.
- Use Cases Typical Networking use cases
¶ User Guide
¶ Administration
Dashboards Display the operational dashboards.
User Groups Permissions and access rights.
Telemetry Help developers understand emerging threats with anonymous telemetry.
Troubleshooting Solutions to common issues.
¶ Feeding Logs
Feed your Defend-O-Tron logs from other devices to enhance the threat detection.
¶ Geek Zone
The Defend-O-Tron is ready for customization.
Armbian Utilities Extra utilities from Armbian.
Hardware Spec What powers the Defend-O-Tron.
Open Hardware Spec Schematics and more.


