The Defend-O-Tron is pre-configured to allow remote log feeding for parsing with Crowdsec via the management interface only.
The Defend-O-Tron is not designed to be a syslog storage and collection server. Sending non security related logs to the device can overwhelm and hinder it's performance. Make sure it's only receiving firewall related logs as was intended. If you require a more robust global logging solution consider Graylog which can filter and forward only firewall related logs to the Defend-O-Tron.
¶ Types of logs to send
The Defend-O-Tron prefers logs that can be parsed via Crowdsec parsers and scenarios by default. Here's a summary of the types of logs that can be fed into the device via syslog.
- Firewall IP connection and access logs
- HTTP and HTTPS Proxy logs (i.e. Traefik, NGINX, HAProxy, Apache)
- Authentication logs (i.e. SSH, PAM)
- Audit logs (i.e. Access, App-armour, Identity, Login, Modules, Time-Changes)
In these examples you will need to have the management IP address of your Defend-O-Tron on hand to enable log forwarding. To maximize performance you should restrict the number of ingress logs to the Defend-O-Tron to between 1-4.
¶ RFC Syslog
Syslog forwarding is available on both Linux and Windows. By default the Defend-O-Tron accepts RFC/IETF compliant syslog messages. For a complete guide on RSyslog configuration visit the documentation site Rocket Syslog
¶ OS Configuration
Add a syslog configuration to the folder in /etc/rsyslog.d to forward to the Defend-O-Tron.
For example, sending only syslogs that have a facility of local2.* you can configure a forwarder as shown on your Linux server.
¶ ~$ nano /etc/rsyslog.d/10-remote.conf
local2.* action(type="omfwd" target="<management ip>" port="514" protocol="udp"
action.resumeRetryCount="25"
queue.type="linkedList"
Docker allows you to configure a logging driver in a few ways.
For a complete guide on Docker logging visit the documentation site Docker Syslog
¶ Docker Compose
You can add a logging driver to your existing Docker Compose file.
logging:
driver: syslog
options:
syslog-address: "udp://<management ip>:514"
syslog-format: "rfc3164"
tag: "my-container logs"
¶ Docker Run
Configure logging directly from the docker run command.
docker run \
--log-driver syslog --log-opt syslog-address=udp://<management ip>:514 \
alpine echo hello world
There are several choices for Windows, listed below are the ones we've tested.
- NXLog Community
The NXLog Community Edition is a high-performance multi-platform log collection solution aimed at solving event log forwarding with a single tool.
Generating syslog and sending over UDP to the management IP address.
¶ nxlog.conf
<Extension _syslog>
Module xm_syslog
</Extension>
<Output out>
Module om_udp
Host <management ip>
Port 514
Exec to_syslog_ietf();
</Output>
- Windows Event Forwarding
Windows Event Forwarding (WEF) reads any operational or administrative event log on a device in your organization and forwards the events you choose to a Windows Event Collector (WEC) server. Note: This is more enterprise level event logging, however the WEC can forward logs to the Defend-O-Tron.
¶ NGINX Direct
For a complete guide on NGINX system logging visit the documentation site NGINX Syslog
The error_log and access_log directives support logging to syslog.
Example syslog configuration in nginx.conf:
user www www;
worker_processes 2;
error_log /var/log/nginx-error.log info;
events {
use kqueue;
worker_connections 2048;
}
server {
root /spool/vhost/data/$host;
access_log syslog:server=<management ip> facility=user,tag=nginx,severity=alert;
...
}
¶ MikroTik Router
For a complete guide on MikroTik system logging visit the documentation site ROS Logging
You can send Mikrotik logs via the default remote logging option under System->Logging->Actions
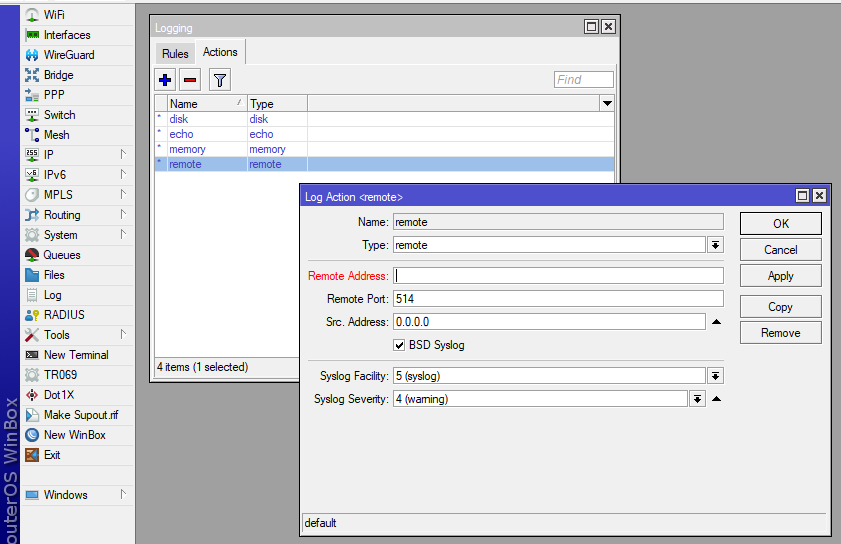
- Configure the Remote Address to point to the Defend-O-Tron management IP address
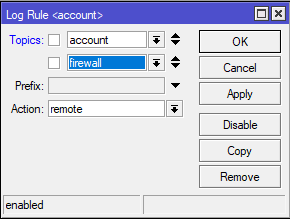
- You can add a rule with both "account" and "firewall" using the action "remote"
¶ Router OS Rules
Here we set the default MikroTik action #3 (remote) to the management IP of the Defend-O-Tron with BSD style syslog and a severity of warning.
The BSD style is mandatory, however the severity is use case specific and the facility should be syslog or local2-5. Syslog Locals 0,1 and 6 are used internally by the Defend-O-Tron.
¶ Terminal config
/system logging action
set 3 bsd-syslog=yes remote=<management ip> syslog-facility=syslog syslog-severity=warning
/system logging
add action=remote topics=firewall
add action=remote topics=account
This type of "mangling" is also referred to as a honeypot since the router in the example is not directly exposing any of those ports.
You can add any mangle rules you like the only requirement is that the log-prefix="" must contain the word BAN in all capitals and have the chain=add-banned. In this example we prefix the ban with the protocol name such as "SSH BAN" this adds the appropriate metadata to Crowdsec.
This example also shows adding the offender to a ban list to be used in filter rules by passing the ISP interface into the mangle rules. Here the gateway connection is maintained via an interface list, however you can also use the upstream interface directly instead.
¶ Terminal config
/ip/firewall/mangle
add action=jump chain=prerouting connection-state=new in-interface-list=gateway-interfaces jump-target=add-banned
add action=add-src-to-address-list address-list=banned-all address-list-timeout=1d chain=add-banned dst-port=22,222 log=yes log-prefix="SSH BAN" protocol=tcp
add action=add-src-to-address-list address-list=banned-all address-list-timeout=1d chain=add-banned dst-port=445 log=yes log-prefix="CIFS BAN" protocol=tcp
add action=add-src-to-address-list address-list=banned-all address-list-timeout=1d chain=add-banned dst-port=1080 log-prefix="SOCKS BAN" protocol=tcp
add action=add-src-to-address-list address-list=banned-all address-list-timeout=1d chain=add-banned dst-port=8291 log=yes log-prefix="WINBOX BAN" protocol=tcp
add action=add-src-to-address-list address-list=banned-all address-list-timeout=1d chain=add-banned dst-port=135-139 log=yes log-prefix="NETBIOS BAN" protocol=udp
add action=add-src-to-address-list address-list=banned-all address-list-timeout=1d chain=add-banned dst-port=123 log-prefix="NTP BAN" protocol=udp
add action=add-src-to-address-list address-list=banned-all address-list-timeout=1d chain=add-banned dst-port=53 log-prefix="DNS BAN" protocol=udp
add action=add-src-to-address-list address-list=banned-all address-list-timeout=1d chain=add-banned dst-port=161 log=yes log-prefix="SNMP BAN" protocol=udp
add action=add-src-to-address-list address-list=banned-all address-list-timeout=1d chain=add-banned dst-port=5060 log=yes log-prefix="SIP BAN" protocol=udp
10:58:28 firewall,info TELNET BAN add-banned: in:vlan10-isp out:(unknown 0), connection-state:new src-mac 10:e8:78:42:85:9e, proto TCP (SYN), 58.47.107.136:43338-><pubic ip>:23, len 60
11:00:09 firewall,info TELNET BAN add-banned: in:vlan10-isp out:(unknown 0), connection-state:new src-mac 10:e8:78:42:85:9e, proto TCP (SYN), 86.127.239.143:44130-><pubic ip>:23, len 44
11:07:26 firewall,info TELNET BAN add-banned: in:vlan10-isp out:(unknown 0), connection-state:new src-mac 10:e8:78:42:85:9e, proto TCP (SYN), 95.67.29.95:24604-><pubic ip>:23, len 40
11:07:56 firewall,info TELNET BAN add-banned: in:vlan10-isp out:(unknown 0), connection-state:new src-mac 10:e8:78:42:85:9e, proto TCP (SYN), 219.115.232.16:60999-><pubic ip>:23, len 40
11:10:08 firewall,info TELNET BAN add-banned: in:vlan10-isp out:(unknown 0), connection-state:new src-mac 10:e8:78:42:85:9e, proto TCP (SYN), 103.103.126.147:15517-><pubic ip>:23, len 44
¶ pfSense Syslog
Configuring pfSense device to forward syslog data to the Defend-O-Tron.
For a complete guide on pfSense system logging visit the documentation site pfSense System Logging
- Log into the pfsense Web Interface.
- Navigate to Status > System Logs > Settings.
- Check Enable Remote Logging.
Note: Select 'BSD (RFC 3164, default)' under Log Message Format. - Enter the management IP address and syslog UDP port(514) of the Defend-O-Tron in the Remote log servers field.
- Click Save.
You need to enable 'Default Allow Logging'.
To enable logging of allowed packets from the default allow rule,
- Navigate to Status > System Logs > Settings tab
- Check Log packets allowed by the rule
- Select Firewall
- Click Save to apply the changes.
¶ Ubiquiti UDM Syslog
Configuration details comming soon